A group of researchers from the Technical University of Darmstadt in Germany has found an exploit in iOS 15 with its new functionality that allows certain wireless chips to remain on even when the device is turned off.
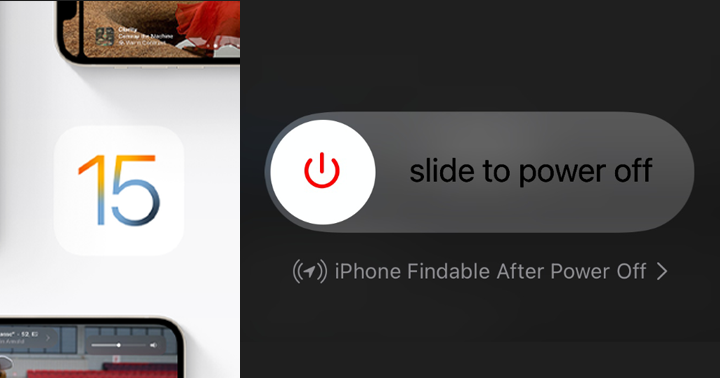
This functionality can help locate the device as it is still able to send signals after shutting down, and hackers may take advantage of it.
The wireless chips that stay on for the app “Find My” to function include Bluetooth, NFC, and ultra-wideband chips maintained in a low-power mode (LPM) state.
In the group’s research paper titled ‘Evil Never Sleeps’ posted last week, they were able to install malware on the Bluetooth chip. Although the claim was mostly theoretical and no evidence yet surface if the kind of exploit has been in the wild.

Moreover, the researchers say that hackers would need to first jailbreak the iPhone before exploiting the Bluetooth chip that would give them access to other places to collect data.
Ultimately, researchers conclude that Apple’s implementation of the new functionality is for the security benefit of the users since it allows them to find a lost or stolen iPhone even when turned off, but it also poses a novelty threat.
“[Low-Power Mode] is a relevant attack surface that has to be considered by high-value targets such as journalists, or that can be weaponized to build wireless malware operating on shutdown iPhones,” the paper stated.
The researchers did disclose their findings to Apple, and the company is yet to have their feedback.
“It may be possible to exploit the Bluetooth chip directly and modify the firmware but the researchers did not do that and there isn’t a known exploit that would currently allow that,” security researcher Ryan Duff said in an online chat with Motherboard after their review of the research paper.

YugaTech.com is the largest and longest-running technology site in the Philippines. Originally established in October 2002, the site was transformed into a full-fledged technology platform in 2005.
How to transfer, withdraw money from PayPal to GCash
Prices of Starlink satellite in the Philippines
Install Google GBox to Huawei smartphones
Pag-IBIG MP2 online application
How to check PhilHealth contributions online
How to find your SIM card serial number
Globe, PLDT, Converge, Sky: Unli fiber internet plans compared
10 biggest games in the Google Play Store
LTO periodic medical exam for 10-year licenses
Netflix codes to unlock hidden TV shows, movies
Apple, Asus, Cherry Mobile, Huawei, LG, Nokia, Oppo, Samsung, Sony, Vivo, Xiaomi, Lenovo, Infinix Mobile, Pocophone, Honor, iPhone, OnePlus, Tecno, Realme, HTC, Gionee, Kata, IQ00, Redmi, Razer, CloudFone, Motorola, Panasonic, TCL, Wiko
Best Android smartphones between PHP 20,000 - 25,000
Smartphones under PHP 10,000 in the Philippines
Smartphones under PHP 12K Philippines
Best smartphones for kids under PHP 7,000
Smartphones under PHP 15,000 in the Philippines
Best Android smartphones between PHP 15,000 - 20,000
Smartphones under PHP 20,000 in the Philippines
Most affordable 5G phones in the Philippines under PHP 20K
5G smartphones in the Philippines under PHP 16K
Smartphone pricelist Philippines 2024
Smartphone pricelist Philippines 2023
Smartphone pricelist Philippines 2022
Smartphone pricelist Philippines 2021
Smartphone pricelist Philippines 2020
rc yap says:
do we still jailbreak phones now?